Join over 500+ Public Entities who work with ResoluteGuard
Comprehensive & Cost-Effective Cybersecurity for Education & Local Government
Enterprise-Grade Cybersecurity for Public Entities—Without Complexity or High Costs.
- Manage cybersecurity without additional hires
- Provide real-time visibility into your cyber posture
- Save time and money by prioritizing effective actions
Learn how to Optimize Cyber Insurance Costs
End-to-End Cybersecurity Implementation and Dedicated Cybersecurity Advisor
Public Entity Guard ™
Cybersecurity Services For Insurance Providers
Government Guard ™
Cybersecurity Services for schools and local government
Your Proactive Cybersecurity Risk Management Solution
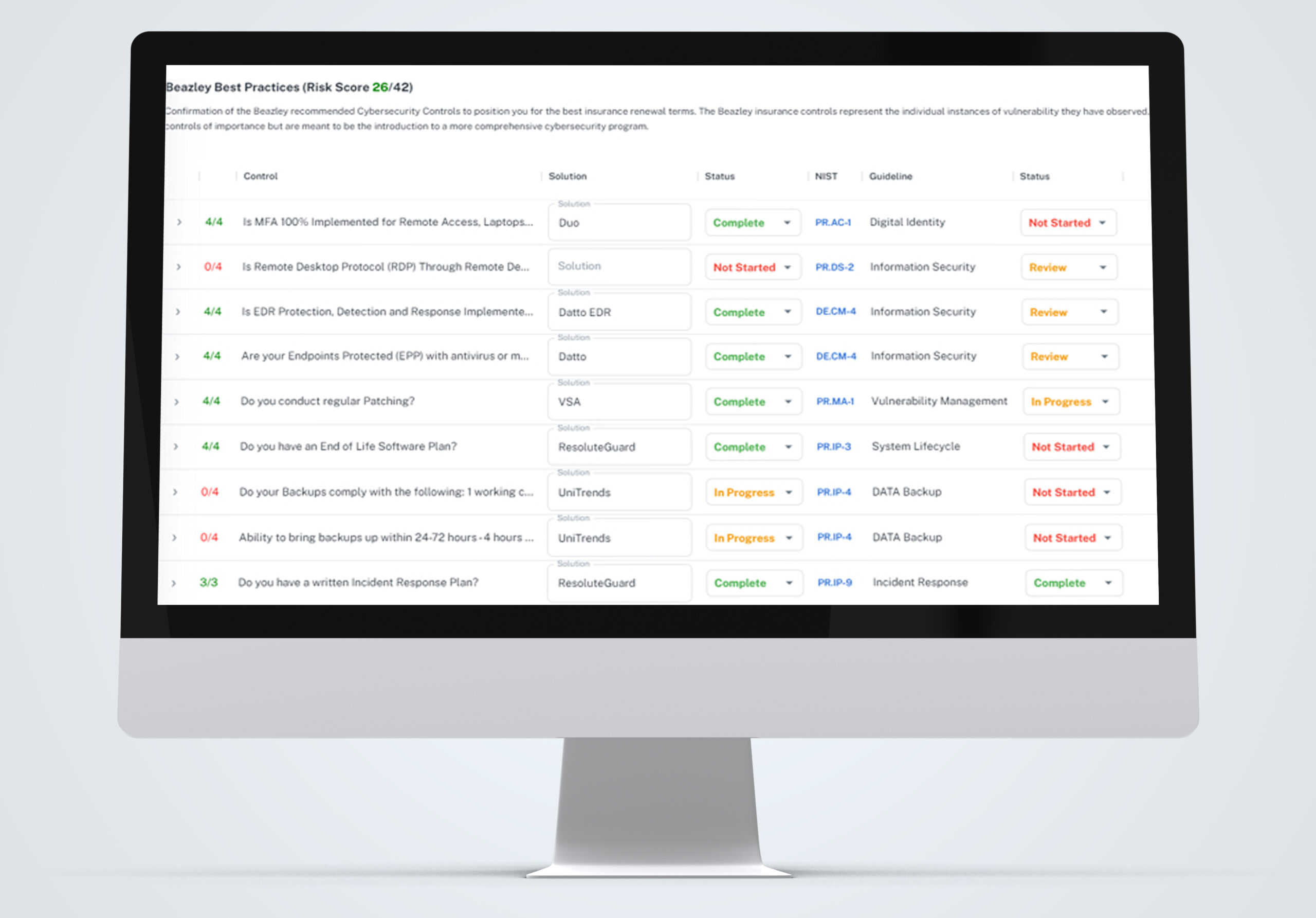
Simplify your cybersecurity planning and governance by leveraging ResoluteGuard’s assessment process, powered by an intuitive application featuring real-time status updates and risk indicators.
- Purpose-Built Cybersecurity Assessment & Planning – Tailored for public entities, using intuitive tools for clear status visibility and progress tracking.
- Seamless, Scalable Implementation – Flexible, phased deployment options suited for organizations with limited IT resources.
- Dedicated Cybersecurity Advisor – Continuous expert guidance from assessment through implementation and ongoing protection.
End-to-End Cybersecurity Implementation Based on Your Infrastructure
ResoluteGuard’s flexible deployment approach allows organizations to implement cybersecurity solutions in a way that fits their needs and available resources.
Flexible Security Solutions:
- Modular security solutions integrate seamlessly with existing protections to close security gaps.
- Continuous monitoring ensures organizations stay ahead of evolving threats.
Scalable Deployment Options:
- Phased Rollout – Implement solutions in stages based on organizational priorities.
- All-in-One Deployment – Achieve full cybersecurity protection with a streamlined approach.

Why Public Entities Need a Dedicated Cybersecurity Advisor?
- Reduces Cybersecurity Risks – Proactively identifies and mitigates cyber threats.
- Ensures Regulatory Compliance – Helps public agencies stay compliant with state & federal cybersecurity laws.
- Improves Incident Response Readiness – Provides a structured approach to handling cyberattacks.
- Protects Public Trust – Ensures citizen data & government services remain secure.
- Strengthens IT & Network Security – Builds a resilient cybersecurity infrastructure for long-term protection.

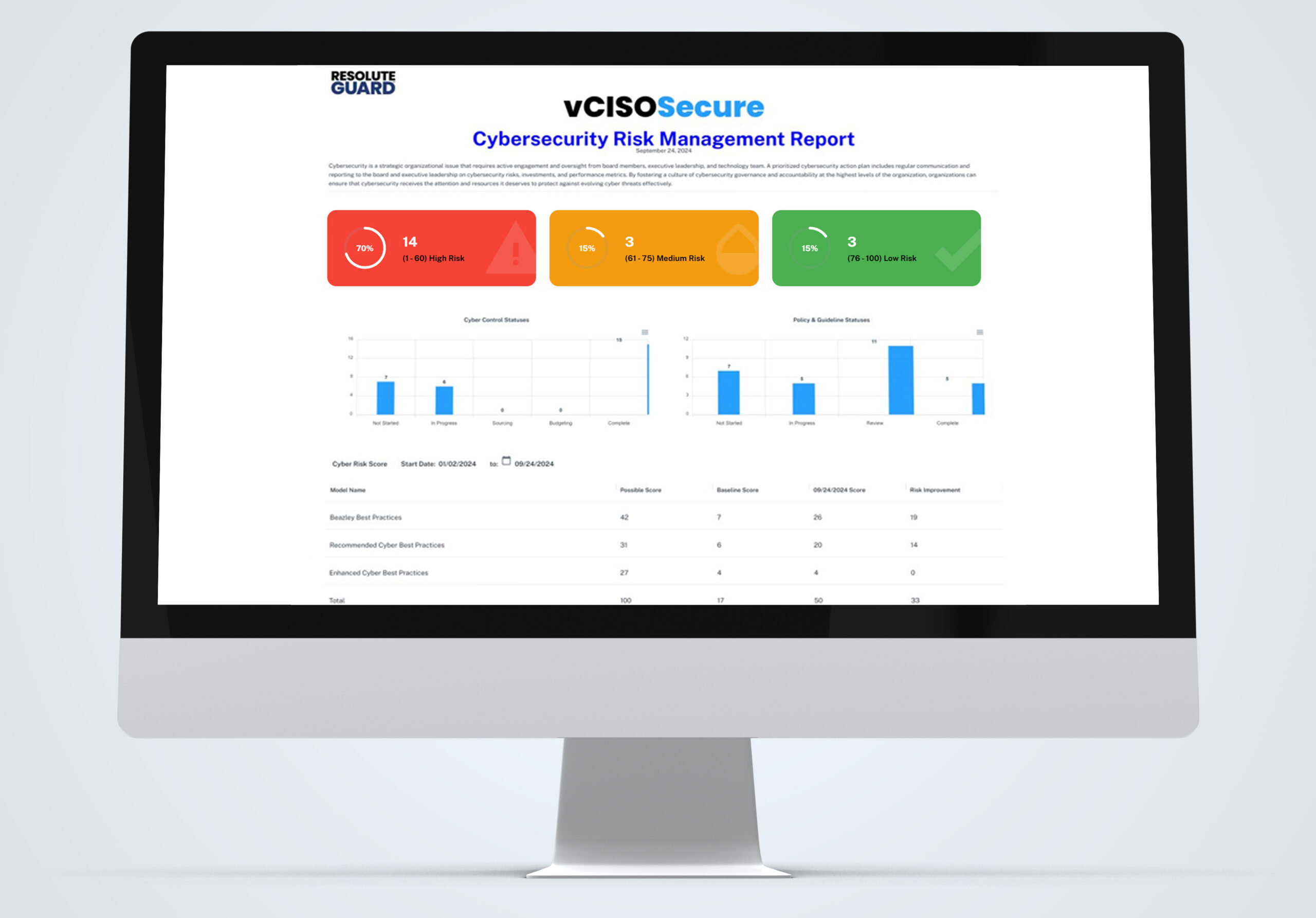
vCISOSecure, our advanced SaaS solution, empowers public entities to strengthen cyber resilience, enhance communication, and achieve cybersecurity objectives.
Backed by expert CISO guidance, our solution helps you continuously improve your security posture over time, manage risks without additional hires, and save resources by prioritizing impactful actions—all through a single, powerful platform.
ResoluteGuard: Protecting Your Community, Not Just Your Data
Before
ResoluteGuard
Financial Losses
Cyberattacks drain budget through theft ransom demands

Reputational Damage
Breaches erode public trust and credibilty.

Legal Penalties
Non-compliance with regulations leads to fines.
Loss of Community Trust
Service Disruptions
Attacks Halt critical operations like schools or utilities .

Data Breaches
Sensitive information get exposed to malicious actors,

Higher Insurance Costs
Increased risks lead to elevated premiums.

Public Safety Risks
Compromised systems expose emergency services to failures.
After
ResoluteGuard

Protected Budgets
Robust defenses prevent financial losses from attacks

Trusted Reputation
Strong security builds public confidence

Regulatory Compliance
Systems meet legal standards, avoiding penalties

Strong Community Confidence

Uninterrupted Services
Resilient systems ensure continuous operations

Secure Data
Encryption and safeguards keep information safe

Lower Insurance Costs
Reduced risks lead to more affordable premiums
Safe Communities
Secure networks protect public safety and well-being
Cybersecurity Services Tailored Specifically for Public Entities
Multi-Factor Authentication: Additional Layer of Security for Your Users
Employee Cybersecurity Training: Your Employees Are Your Organization’s First Line of Defense Against Cyber Threats
Remote Monitoring & Management (RMM): Streamline IT Management
Backup and Recovery: Securely Store Critical Data
Automatic External Penetration Testing: Proactive Defense for Your Organization
Email Security: Safeguard Your Organization from Email Threats
24/7 Threat Monitoring with MDR/XDR: Enhance Threat Detection & Response
Protect Your Devices with EDR (Endpoint Detection and Response)
Third-Party Risk Management (TPRM): Safeguarding Your Organization from External Threats
Compliance and Regulatory Requirements for Public Entities
Cybersecurity Statistics from our Public Entity Customer Base
We’ve exceled our experience in a wide range of industries to bring valuable insights and provide our customers.
Cybersecurity Professionals reported they are understaffed
Days Cyber Criminals have access to Sensitive Data
Cyber attacks per year
New Vulnerabilities Reported Daily
Learn Why 500+ Public Entities Trust ResoluteGuard!

Email a Cyber Specialist
Speak with a ResoluteGuard specialist to learn how you can improve your cybersecurity posture.

Schedule a Call
Learn in real-time how ResoluteGuard can provide cybersecurity protection.

Give Us a Call!
Can’t wait to speak with us? Give us a call directly to learn how we can improve your cybersecurity posture.
