Customized SMART-Cyber Action Plan
You must have a plan with a strategy of continuously improving your cyber-security profile to meet todays ever-evolving cyber security challenges.
This plan needs to align your executive governance administrative and technical resources/activities to your plan/strategies. Aligns Your Executive Governance, Administrative and Technical Activities with Regulatory and Insurance Requirements and/or Considerations To Guard Against A Cyber Disruption Of Service.
S-CAP aligns your team members by using easy to use, easy to understand Cyber Action Plan so adoption is immediate, we make it even easier by taking the tech talk out of the language so everyone can understand and be on same page in support of your cyber plan and strategy.
SMART- Cyber Action Plan supports you continuously improving your cyber readiness to keep an incident from becoming a disaster.
S-CAP Strategy
1
Verify and document compliance with Insurance requirements
This is to best position you for favorable insurance renewal terms AND to be sure you are in compliance if a claim is required
In the industry a common phase is "it is not if but when" you will be subject to a cyber/attack, which speaks about the ever-evolving challenges of keeping your network and your people secure in their practices.
It is critically important to be ready to respond to keep a cyber-incident from becoming a "disruption of critical services disaster" which is when the ransomware and Organization response cost and time goes up exponentially.
This is why our S-CAP prioritizes doing everything you can as SMART as you can to be ready to respond and keep an incident from becoming a disaster.
Alignment with regulatory controls, for which the National Institute of standards cyber security framework is the gold standard….and other Regulatory Compliance standards.
As government regulations evolve and potential government monetary support becomes available, it will be based on NIST-CSF so S-CAP aligns all activities to this standard so you are in the best position to meet government standards and potentially qualify for monetary support.
2
Prioritized Cyber Control Requirements & Best Practices
In this phase, we meet with your technical/ IT teams to obtain the information needed to assess technical gaps and risks. This National Institute of Standards and Technology (NIST) Cybersecurity Framework-based workshop assesses areas of security in a broad-based evaluation resulting in a baseline from which we create your cybersecurity strategy matrix.
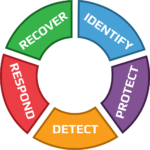
The NIST Cybersecurity Framework
3
Vendor Solutions Recommendations
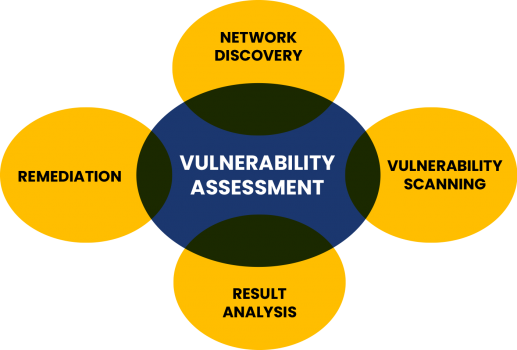
Our Cyber Risk Assessment includes a series of vulnerability scans. These scans help to identify risks such as vulnerabilities, server misconfigurations, and sensitive data exposures, all of which provide us with the information essential to developing your cybersecurity strategy.
4
Maintenance to Support Solutions implemented
This score is a baseline that helps establish your organization’s current level of cybersecurity. It allows the ResoluteGuard team to create a cybersecurity strategy that leverages your current information technology investments to best optimize the balance of cost and risk.
5
Comprehensive Internal & External Risk Profile Assessments
Each deliverable includes a description of findings including recommendations on how to remediate these issues. It focuses on your top risks and prioritizes findings by cost, effort, impact, and probability of risk.
6
Continuous, monthly, quarterly, semi-annual, annual scans
A cyber risk assessment has great value when it provides actionable steps to remediate issues. ResoluteGuard provides you with a cybersecurity strategy you can execute on the next day. Since ResoluteGuard is an independent firm, we only recommend the controls you need.
7
Key to the platform
A cyber risk assessment has great value when it provides actionable steps to remediate issues. ResoluteGuard provides you with a cybersecurity strategy you can execute on the next day. Since ResoluteGuard is an independent firm, we only recommend the controls you need.
Specifically, compliance frameworks include:
HIPAA
CMMC
SOX
PCI DSS
SOC Reports
ISO 27000 Family
GDPR
We are Trusted
By X Companies

Moonkle LTD,
Client of Company
SoftTech,
Manager of Company
Moonkle LTD,
Client of Company
