Local Government
- Home
- Local Government
Local Governments face greater cyber risks than many other public entities due to their vast networks, sensitive data, and limited resources for robust cybersecurity measures.
Is your city/county doing enough to reasonably protect its residents?
Unleash the Power of Proactive Cyber Defense in Your City/County
Learn How We Can Work With Your City/County:
In today’s evolving digital landscape, local government must prioritize understanding the status of their cybersecurity practices. Proactively monitoring and aligning with cyber best practices is essential to maturing your cyber posture, safeguarding sensitive data, and ensuring uninterrupted environments.
Whether you manage your network in-house or maintain IT vendor support contracts, we provide a SaaS solution, vCISOSecure, that enables your city/county to effectively monitor and manage your cybersecurity posture.
Powered by automation, our core service “Cybersecurity Risk Management Solution” is purpose-built to create a defensible cybersecurity risk management platform that bolsters the organization’s Cyber resilience.
SMART-Cyber Action Plan™
Customized plan & strategy aligned with your insurance cyber best practices with a focus on continuous improvement and actionable insights. vCISOSecure ensures that you are well-equipped to maintain robust cyber defenses and meet evolving best practices.
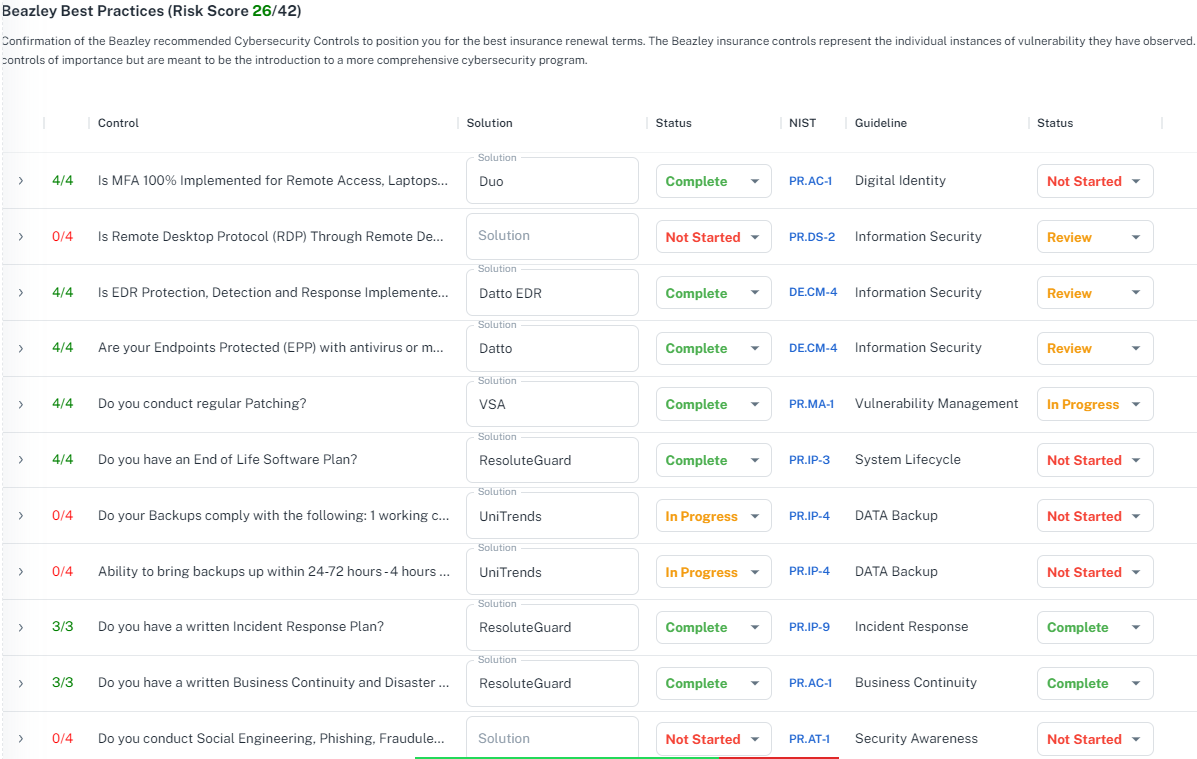
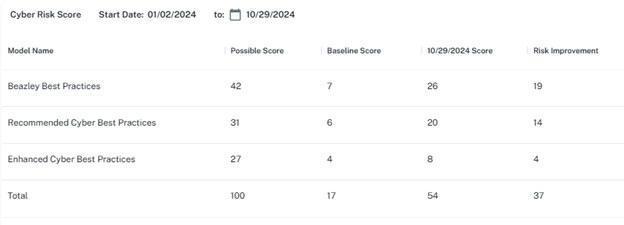
Cybersecurity Dashboard
Dashboard displaying your cyber risk score and top assigned priorities provides critical, real-time visibility into their cybersecurity posture. Highlighting top assigned priorities ensures that you focus on the prioritizing actions and improving resource allocation.

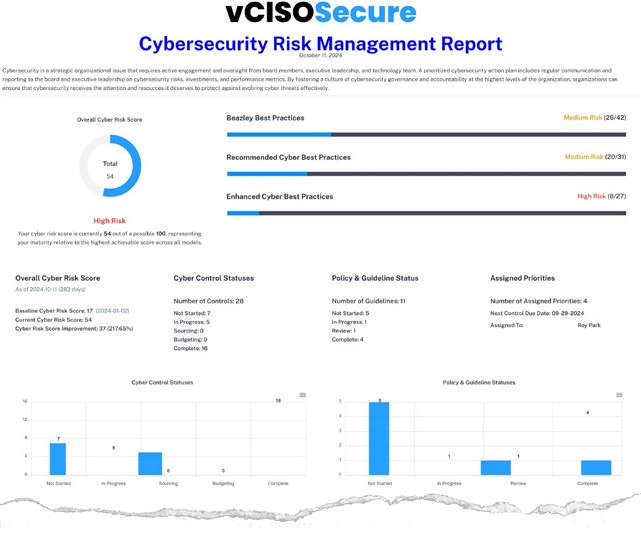
Cybersecurity Risk Management Executive Summary
Provides real-time analysis of your current cybersecurity posture, provides a clear overview of cybersecurity risks and statuses, facilitating better communication between IT teams and Executive leadership.
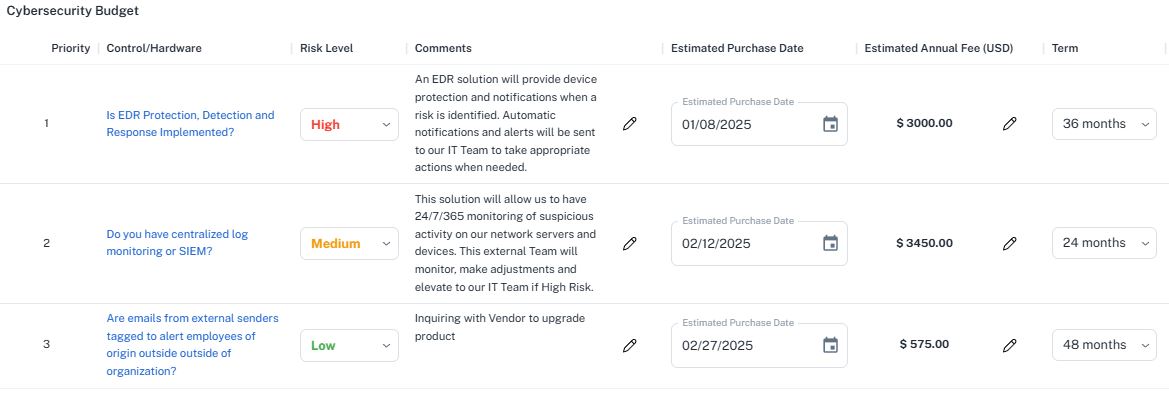
Cybersecurity Budget
Easily budget for cybersecurity solutions prioritized by high-risk areas and the funds needed to address them. Share clear, actionable insights with leadership to support informed decision-making and focus on critical cyber defense priorities
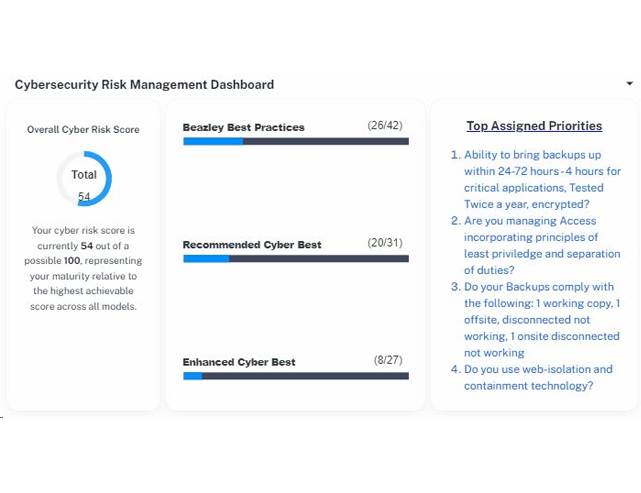
Policy/Guidelines Report
With over 24 pre-built policy templates, you gain a significant advantage in developing essential cybersecurity documentation. The key focus areas include building an Incident Response Plan, a Business Continuity and Disaster Recovery Plan, and an Information Security Policy.

Risk Assessment and Vulnerability Analysis

Network Security and Infrastructure Protection
Cybersecurity Training and Awareness Programs
Cybersecurity Compliance Audits for Grant and Funding Requirements

Average Incident Cost
$175,000
Average Downtime
8.93 Days
Number of Attacks
2023 increased 30%
Automatic Notifications
Rules-based notifications to inform technical teams and administrators of current status and actions required to continuously improve your cyber posture.
Ongoing CISO Team Knowledge & Guidance
We know Public Entities! ResoluteGuard’s Cyber experts provide expert cybersecurity guidance to safeguard your assets and protect against vulnerabilities.
Comprehensive Vulnerability Scans
Continuous external vulnerability scans—including internal network scans and penetration testing—identify cyber risks across multiple attack vectors. Detected issues are prioritized by risk severity, with actionable steps provided to swiftly remediate vulnerabilities.
Cyber Solutions Recommendations
Based upon the current profile of your cyber posture, we recommend tailored solutions to meet their specific needs. ResoluteGuard provides you with best-in-class product solutions at a fraction of the cost.
Comprehensive Protection
A multi-layered approach that addresses vulnerabilities, guides tailored responses, and establishes standardized practices
Risk Reduction
Proactive identification and mitigation significantly reduce the risk of successful cyber-attacks
Empowerment
A multi-layered approach that addresses vulnerabilities, guides tailored responses, and establishes standardized practices
Peace of Mind
Knowing that your K-12 district is fortified with a robust cybersecurity program that evolves with the threat landscape
Get Started and Learn More Today

Email a Specialist
Speak with a ResoluteGuard specialist to learn how you can improve your cybersecurity posture.

Schedule a Demo
Learn in real-time how ResoluteGuard can provide cybersecurity protection.

Give Us a Call!
Can’t wait to speak with us? Give us a call directly to learn how we can improve your cybersecurity posture.
