Are All of Your Access Points Using Multi-Factor Authentication?
Multi-Factor Authentication (MFA) is a critical layer of security that helps protect sensitive systems, networks, and data from unauthorized access. It requires users to provide two or more verification factors to gain access, making it significantly more difficult for malicious actors to compromise accounts, even if they have obtained the user’s password. Here’s why ensuring all of your access points use MFA is essential, how to implement it, and best practices for comprehensive MFA deployment.
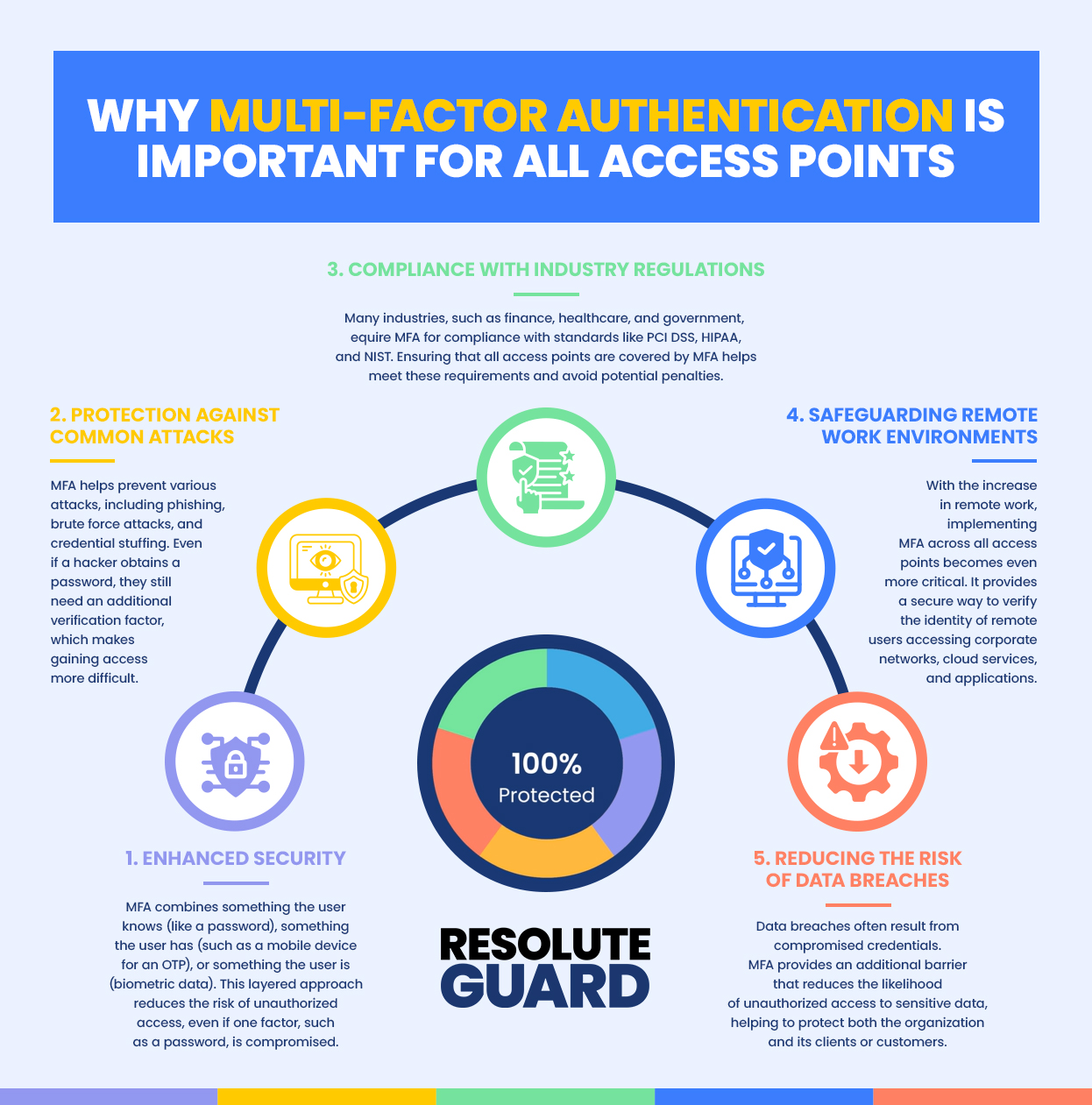
Why Multi-Factor Authentication is Important for All Access Points
- Enhanced Security
MFA combines something the user knows (like a password), something the user has (such as a mobile device for an OTP), or something the user is (biometric data). This layered approach reduces the risk of unauthorized access, even if one factor, such as a password, is compromised. - Protection Against Common Attacks
MFA helps prevent various attacks, including phishing, brute force attacks, and credential stuffing. Even if a hacker obtains a password, they still need an additional verification factor, which makes gaining access more difficult. - Compliance with Industry Regulations
Many industries, such as finance, healthcare, and government, require MFA for compliance with standards like PCI DSS, HIPAA, and NIST. Ensuring that all access points are covered by MFA helps meet these requirements and avoid potential penalties. - Safeguarding Remote Work Environments
With the increase in remote work, implementing MFA across all access points becomes even more critical. It provides a secure way to verify the identity of remote users accessing corporate networks, cloud services, and applications. - Reducing the Risk of Data Breaches
Data breaches often result from compromised credentials. MFA provides an additional barrier that reduces the likelihood of unauthorized access to sensitive data, helping to protect both the organization and its clients or customers.
How to Ensure All Access Points are Using Multi-Factor Authentication
To implement MFA across your organization, you’ll need to conduct a comprehensive review of all access points and determine where MFA is essential. Here’s a step-by-step approach to achieving full MFA coverage:
- Identify All Access Points
- Inventory Systems and Applications
List all the systems, applications, databases, and network access points that require user authentication. This includes email platforms, VPNs, cloud services, internal systems, and remote access portals. - Assess High-Risk Access Points
Prioritize access points that handle sensitive information, such as financial systems, customer data, or intellectual property. These should be the first to receive MFA implementation due to their higher risk.
- Choose the Right MFA Methods
- One-Time Passwords (OTP)
OTPs are temporary codes sent to the user’s mobile device or email. They’re commonly used for MFA as they’re both secure and convenient. - Biometrics
Biometrics use unique physical characteristics, such as fingerprints or facial recognition, to authenticate users. These methods are particularly useful for physical access points and mobile devices. - Push Notifications
Push notifications are sent to a user’s smartphone, prompting them to approve or deny an access request. This method is both secure and user-friendly. - Hardware Tokens
Hardware tokens, such as USB security keys or smart cards, provide a highly secure MFA option. These tokens are especially useful for securing critical access points. - Authentication Apps
Apps like Google Authenticator, Microsoft Authenticator, or Duo Mobile generate time-based OTPs for user verification. These apps are reliable and work even when a user’s phone lacks network connectivity.
- Implement MFA for High-Impact Systems First
- Prioritize Sensitive Systems
Start with critical systems, such as financial systems, cloud platforms, email accounts, and VPNs. By implementing MFA for these systems, you secure access to your organization’s most valuable data. - Apply MFA to Remote Access Tools
Ensure that remote access tools, like VPNs and remote desktop applications, have MFA enabled. These tools are commonly targeted by cybercriminals, making them a high priority. - Secure Cloud-Based Applications
Many organizations rely on cloud applications like Office 365, Salesforce, and G Suite. Ensure MFA is enabled for all users accessing these applications to protect cloud-based data.
- Enforce MFA Across All User Types
- Employees
Require MFA for all employees, regardless of their role. This includes temporary staff and contractors who may have access to your systems. Enforcing MFA at the organizational level ensures no access point is overlooked. - Administrators and IT Staff
Administrators typically have elevated access to systems and data. Implementing MFA for admin accounts is essential as they’re prime targets for cybercriminals. - Vendors and Third-Party Users
If vendors or third-party partners access your systems, require MFA for these users as well. Third-party access can be a vulnerability, so extending MFA requirements to them is a best practice.
- Integrate MFA with Single Sign-On (SSO)
- Streamline Access with SSO
Implementing Single Sign-On (SSO) allows users to access multiple systems with a single set of credentials. Integrate MFA with SSO for added security, requiring an additional verification step when accessing critical applications. - Simplify User Experience
SSO combined with MFA enhances security while simplifying the login process for users. Rather than logging in separately to each application, users complete one MFA step at the start of their session, improving convenience.
- Train Users on the Importance of MFA
- Educate Employees on MFA Benefits
Ensure all users understand the importance of MFA and how it protects both their accounts and the organization. Explain that MFA reduces the likelihood of account compromise and helps protect sensitive data. - Provide Instructions on MFA Use
Offer clear instructions on how to use each MFA method, whether it’s entering an OTP, approving a push notification, or using a hardware token. Training can prevent user frustration and reduce helpdesk requests. - Encourage Reporting of Suspicious Activity
Teach users to report any unusual MFA prompts they receive. Unexpected MFA requests could indicate that a cybercriminal is attempting to access their account, and quick reporting helps contain potential incidents.
- Monitor and Audit MFA Usage
- Use an Authentication Monitoring System
Track login attempts, including successful and failed MFA attempts, through an authentication monitoring system. Look for suspicious patterns, such as multiple failed attempts or access requests from unfamiliar locations. - Conduct Regular MFA Audits
Review your MFA deployment periodically to ensure it remains effective. Confirm that all high-risk access points are covered by MFA and that new systems or applications are included in the MFA policy. - Adjust MFA Settings Based on Risk Levels
For highly sensitive systems, consider stricter MFA requirements, such as multiple factors or additional monitoring. For lower-risk systems, standard MFA methods may be sufficient.
Best Practices for Comprehensive MFA Coverage
- Implement a “Zero Trust” Security Model
The Zero Trust model assumes that all users and devices, both inside and outside the network, must be verified. By enforcing MFA for all access points, you strengthen the Zero Trust model within your organization. - Require MFA for Password Resets
Use MFA to verify user identities during password resets. This adds an extra layer of protection, as attackers commonly attempt to reset passwords to gain unauthorized access. - Consider Adaptive MFA Based on Risk
Adaptive MFA, or risk-based MFA, adjusts the verification requirements based on the context. For example, access from a trusted device may require a single MFA factor, while access from an unrecognized location may require additional verification. - Stay Informed of Emerging MFA Technologies
Keep up-to-date with new MFA solutions and technologies. As cyber threats evolve, so do the tools available for securing access points. Explore new MFA methods, such as behavioral biometrics, that provide continuous authentication.
- Leverage MFA for Privileged Access Management (PAM)
- Enforce MFA on Privileged Accounts:
Privileged accounts, such as those held by system administrators, database managers, and IT personnel, have higher access levels and often control critical systems. Implementing MFA on these accounts provides an added layer of security, helping prevent unauthorized access and insider threats. - Integrate MFA with PAM Solutions:
Many Privileged Access Management (PAM) solutions offer MFA capabilities. Using a PAM solution with integrated MFA allows you to control and monitor privileged accounts more effectively, tracking access and enforcing strict verification protocols. - Use Just-In-Time (JIT) Access with MFA:
JIT access temporarily grants elevated privileges to users only when needed. Enforcing MFA on JIT access requests ensures users verify their identity before receiving temporary access, reducing the window of vulnerability.
- Extend MFA to APIs and Service Accounts
- Secure APIs with MFA:
If your systems and applications use Application Programming Interfaces (APIs) to communicate and share data, consider implementing MFA for API access. While traditional API access uses tokens, incorporating MFA helps ensure that only authorized services can access these critical functions. - Implement Service Account Protection:
Service accounts often have elevated permissions and are used for system-to-system communication. By adding MFA, or by applying security policies that mimic MFA, you can protect these accounts from being compromised and misused by malicious actors. - Use API Gateways with Built-In MFA Capabilities:
Some API gateways provide built-in MFA, adding a layer of security for accessing services. Use these tools to enforce MFA for all API calls, ensuring that only authenticated and authorized calls are executed.
- Apply MFA to Third-Party Applications and Integrations
- Require MFA for All Third-Party Vendors:
Vendors and third-party applications often have access to sensitive data and systems, making them potential entry points for attackers. Require MFA for all third-party integrations and vendor accounts to reduce this risk. - Use OAuth with MFA for External Applications:
OAuth allows for secure token-based authentication, often used for third-party applications. Combining OAuth with MFA ensures that access tokens are issued only to verified users or systems. - Implement Conditional Access Policies for Third Parties:
Enforce conditional access policies based on risk levels for third-party applications. For example, enable additional MFA requirements for access attempts from unfamiliar IP addresses or regions, reducing the likelihood of unauthorized access from high-risk areas.
- Secure Mobile Devices and Remote Work Environments with MFA
- Enable MFA for Mobile Device Management (MDM):
MDM solutions allow IT teams to manage and secure mobile devices used by employees. Enforce MFA for accessing MDM platforms to ensure that only authorized administrators can manage devices remotely. - Implement MFA for Remote Desktop Access (RDP):
Many organizations use RDP for remote work access. Requiring MFA for RDP sessions provides a critical security layer that reduces the risk of unauthorized remote access, particularly from external or high-risk IP addresses. - Require MFA for BYOD Programs:
For bring-your-own-device (BYOD) environments, mandate that all personal devices used for work have MFA enabled. This helps protect sensitive data and systems when accessed from personal devices, minimizing the risk of data breaches from unsecured devices.
- Use MFA in Conjunction with Identity and Access Management (IAM)
- Integrate MFA with IAM Solutions:
Identity and Access Management (IAM) solutions streamline user authentication and access control across the organization. Integrate MFA with IAM to enforce consistent access policies and improve security for all users and applications. - Automate User Provisioning with MFA Requirements:
When provisioning new users, configure IAM solutions to automatically enable MFA. This ensures that all new accounts are secured from the start and eliminates the risk of human error or oversight. - Utilize Role-Based Access Control (RBAC) with MFA:
Implement RBAC within your IAM framework to assign permissions based on user roles. Combine RBAC with MFA to enhance security, ensuring that only authorized individuals can access resources according to their role and privileges.
- Apply Adaptive or Risk-Based MFA
- Adjust MFA Based on Contextual Factors:
Adaptive MFA evaluates risk factors such as device type, location, and login behavior. Use this approach to enforce stricter MFA requirements when unusual activity is detected, such as access from an unrecognized device or geographic location. - Enable Step-Up Authentication:
Step-up authentication adds an additional layer of verification based on risk level. For example, users might only be prompted for MFA when accessing sensitive information or high-risk systems, providing a balance between security and user convenience. - Use Geolocation-Based MFA:
Require additional verification if users attempt to access systems from new or high-risk locations. This approach ensures that access attempts from unfamiliar regions are verified, reducing the risk of unauthorized access.
- Monitor MFA Activity and Respond to Anomalies
- Track MFA Usage with Logs and Analytics:
Regularly monitor MFA usage to identify patterns and anomalies. By reviewing logs, you can detect suspicious activity, such as repeated failed MFA attempts or access attempts from unfamiliar locations. - Implement Alerts for Suspicious MFA Activity:
Configure your monitoring system to trigger alerts for abnormal behavior, such as multiple failed MFA attempts, access from high-risk locations, or unusual login times. This allows for real-time response to potential security incidents. - Conduct Regular Security Audits on MFA Policies:
Perform periodic security audits to evaluate the effectiveness of your MFA policies. Review your access points, check for compliance, and make adjustments to address any vulnerabilities or gaps in coverage.
- Automate MFA Configuration and Enforcement
- Use Security Automation Tools for MFA Deployment:
Security automation tools simplify the deployment and enforcement of MFA across your organization. Automating MFA configuration for new users and applications ensures that every access point is covered without manual intervention. - Create Automatic Expiry for MFA Tokens:
For OTP or session-based MFA, configure tokens to expire after a certain period. Automating expiration times ensures that even if a token is compromised, it cannot be reused after it has expired. - Automate MFA Policy Compliance Checks:
Use automation to conduct routine compliance checks, ensuring that MFA is enabled across all required access points. Automated compliance checks help identify areas where MFA is not enforced, allowing for quick remediation.
- Plan for Backup MFA Options and Account Recovery
- Offer Multiple MFA Methods for Flexibility:
Provide users with several MFA options, such as SMS, email, and authentication apps. Having backup methods ensures that users can still access systems if one MFA method fails or if they lose access to a primary authentication method. - Set Up a Secure Account Recovery Process:
Implement a secure account recovery process that includes MFA. For instance, users who forget their primary authentication method can verify their identity through a secondary MFA factor before resetting their credentials. - Establish Clear Policies for MFA Device Replacement:
Define policies for replacing lost or broken devices used for MFA. For example, if a user’s phone with an authenticator app is lost, have a secure process in place for transferring the MFA setup to a new device.
- Implement MFA for IoT Devices and Industrial Control Systems (ICS)
- Enable MFA for IoT Device Access:
Internet of Things (IoT) devices are increasingly connected to corporate networks. Require MFA for accessing IoT management systems to prevent unauthorized access and reduce the risk of attacks on these devices. - Use MFA for ICS and Operational Technology (OT):
Industrial Control Systems (ICS) and OT are critical in sectors like manufacturing and energy. Applying MFA to these systems helps protect them from unauthorized access and ensures that only authorized personnel can control critical infrastructure. - Monitor Access to Connected Devices:
Track and log all access to IoT and ICS devices, using MFA as an additional security layer. Regularly review access logs to detect any unusual activity and confirm that all access attempts are authorized.
- Test and Update MFA Policies Regularly
- Conduct Routine Penetration Testing:
Penetration testing helps identify vulnerabilities in your MFA setup. By simulating attacks, you can assess how well your MFA policies hold up against potential threats and make improvements based on the findings. - Stay Updated on New MFA Technologies:
MFA technology continues to evolve. Stay informed about emerging MFA options, such as biometric advancements or hardware token innovations, to enhance your security posture as new technologies become available. - Review and Adjust MFA Policies as Needed:
Periodically review your MFA policies to ensure they remain effective and relevant. As your organization changes, adjust your MFA settings, methods, and policies to address new security requirements and potential risks.
Conclusion: Building a Robust MFA Strategy
Multi-Factor Authentication is a powerful tool for protecting access points across your organization. By implementing MFA on all systems, monitoring usage, and staying proactive about updates and improvements, you significantly reduce the risk of unauthorized access. A comprehensive MFA strategy that includes adaptive authentication, secure account recovery, and coverage for IoT and industrial control systems strengthens your security posture and helps safeguard your organization’s data, assets, and reputation. By integrating MFA into a broader security framework, you can create a resilient defense against evolving cyber threats and enhance your overall cybersecurity strategy.

